- It is the method by which plaintext or any other type of data is converted from a readable form to an encoded version that can only be decoded by another entity if they have access to a decryption key.
- It is one of the most important methods for providing data security, and protection of data transmitted across networks.
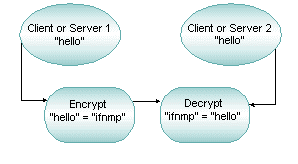
How encryption works:
- Data is encrypted using an encryption algorithm and an encryption key.
- This process generates encrypted data that can only be viewed in its original form if decrypted with the correct key.
- Decryption is simply the inverse of encryption, following the same steps but reversing the order in which the keys are applied.
- Most widely used encryption algorithms fall into two categories: symmetric and asymmetric.
- Symmetric encryption:
- It is also referred to as secret key.
- Symmetric-key encryption use the same secret key for encrypting and decrypting a message or file.
- While symmetric-key encryption is much faster than asymmetric encryption, the sender must exchange the encryption key with the recipient before he can decrypt it.

- It is referred to as public-key encryption.
- It uses two different keys, one public and one private.
- The public key, as it is named, may be shared with everyone, but the private key must be protected.
- The RSA algorithm is a system for public-key encryption that is widely used to secure sensitive data, especially when it is sent over an insecure network like the internet.

Uses:
- It is widely used on the internet to protect user information being sent between a browser and a server, including passwords, payment information and other personal information that should be considered private.
- It is used in ATMs.
- Organizations and individuals also commonly use encryption to protect sensitive data stored on computers, servers and mobile devices like phones or tablets.

